LDAP, or Lightweight Directory Access Protocol, is a protocol for managing related information from a centralized location through the use of a file and directory hierarchy.
It functions in a similar way to a relational database in certain ways, and can be used to organize and store any kind of information. LDAP is commonly used for centralized authentication.
In this guide, we will cover how to install and configure an OpenLDAP server using osixia OpenLdap docker image on Ubuntu. We will populate it with some users and groups.
Run Osixia OpenLDAP Docker Image
First, you should have Docker installed on your Ubuntu. https://docs.docker.com/install/linux/docker-ce/ubuntu/ , is the official link for installing Docker. Don’t forget to follow post-installation steps in the end.
Then simply run the following command from terminal.
docker run -p 389:389 --name ldap-service --hostname ldap-service --env LDAP_ORGANISATION="ScytaleLabs" --env LDAP_DOMAIN="scytalelabs.com" \
--env LDAP_ADMIN_PASSWORD="adminPassword" --env LDAP_BASE_DN="dc=scytalelabs,dc=com" --volume /data/slapd/database:/var/lib/ldap \
--volume /data/slapd/config:/etc/ldap/slapd.d --detach osixia/openldap:1.3.0It will fetch the image and start the docker container. Organization name, domain, admin password and base domain name should be provided with environment flag. Port is exposed for accessing the container from another machine and volumes are mapped so your data remains in persistent state.
For additional configuration you can visit the official GitHub repository here.
Run Osixia phpLDAPadmin Docker Image
There is another Osixia Docker image which provides GUI for its OpenLDAP image, very useful for populating users and groups into OpenLDAP visually.
docker run --name phpldapadmin-service --hostname phpldapadmin-service --link ldap-service:ldap-host --env PHPLDAPADMIN_LDAP_HOSTS=ldap-service --detach osixia/phpldapadmin:0.9.0This command will fetch the image and run the container, which will be linked to the previously running container through the link flag.
docker inspect -f "{{ .NetworkSettings.IPAddress }}" phpldapadmin-serviceThis command will give you the IP-Address for phpldapadmin-service container, Go to: https://IP_Address and you will get this on your screen.

OpenLDAP & phpLDAPadmin in 1 go
Example script:
#!/bin/bash -edocker run -p 389:389 --name ldap-service --hostname ldap-service --env LDAP_ORGANISATION="ScytaleLabs" --env LDAP_DOMAIN="scytalelabs.com" \
--env LDAP_ADMIN_PASSWORD="adminPassword" --env LDAP_BASE_DN="dc=scytalelabs,dc=com" --volume /data/slapd/database:/var/lib/ldap \
--volume /data/slapd/config:/etc/ldap/slapd.d --detach osixia/openldap:1.3.0docker run --name phpldapadmin-service --hostname phpldapadmin-service --link ldap-service:ldap-host --env PHPLDAPADMIN_LDAP_HOSTS=ldap-service --detach osixia/phpldapadmin:0.9.0PHPLDAP_IP=$(docker inspect -f "{{ .NetworkSettings.IPAddress }}" phpldapadmin-service)echo "Go to: https://$PHPLDAP_IP" Log Into the Web Interface
Click on the “login” link on the left-hand side.
You will receive a login prompt. The correct Login DN (distinguished name) should be “cn=admin,dc=scytalelabs,dc=com”.
Enter the password you selected during our configuration time thorough environment variable LDAP_ADMIN_PASSWORD.
You will be presented with a rather sparse interface initially.
If you click on the “+” next to the domain components (dc=scytalelabs,dc=com), you will see the admin login we are using.
Add Organizational Units, Groups, and Users
LDAP is very flexible. You can create hierarchies and relationships in many different ways, depending on what kind of information you need accessible and what kind of use case you have.
We will create some basic structure to our information and then populate it with information.
Create Organizational Units
First, we will create some categories of information where we will place the later information. Because this is a basic setup, we will only need two categories: groups and users.
Click on the “Create new entry here” link on the left-hand side.
Here, we can see the different kinds of entries we can create.
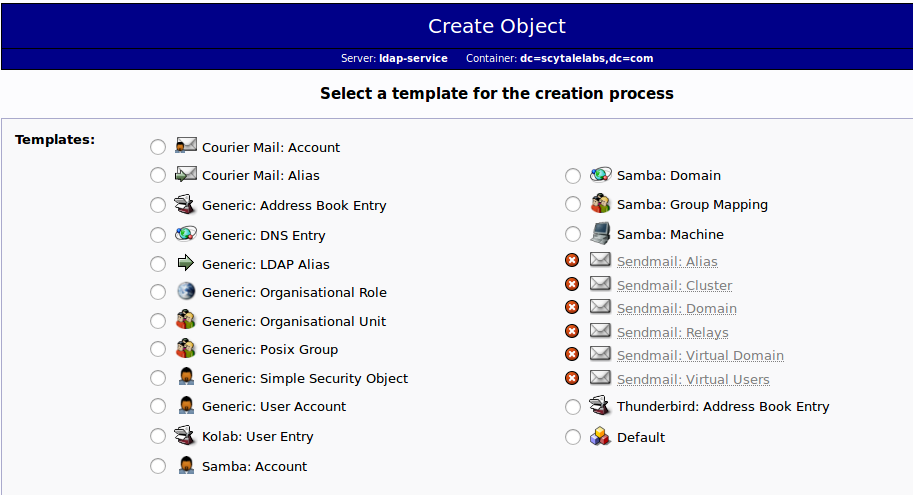
Because we are only using this as an organizational structure, rather than an information-heavy entry, we will use the “Generic: Organizational Unit” template.
We will be asked to create a name for our organizational unit. Type “groups”:
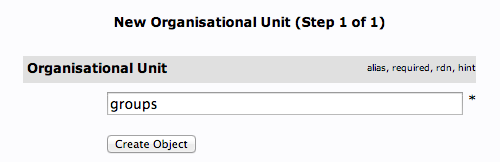
We will then need to commit the changes.
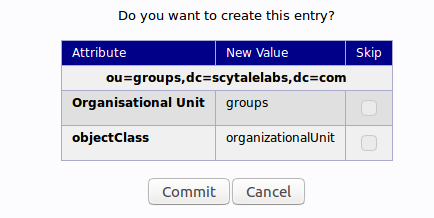
When this is complete, we can see a new entry on the left-hand side.
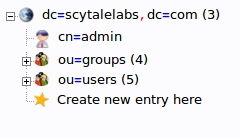
We will create one more organizational structure to get ourselves going. Repeat the procedure, but this time, use the name “users”.
When you are done, you should have something that looks like this:
Create Groups
We will be creating four different groups that could be used to organize users into different “access” groups based on the privileges they require.
We will create an “issuer” group, an “employer” group, a “revoker” group, a “student” group. We could then allow members of different groups to authenticate if we set up client LDAP authentication.
We want to create the groups within the “groups” organizational unit. Click on the “groups” category we created. In the main pane, click on the “Create a child entry” within the groups category.
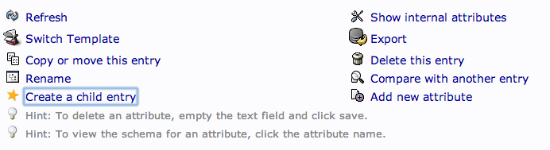
This time, we will choose the “Generic: Posix Group” category.
Fill in “issuer” as the group name. Click “Create Object” and then confirm on the next page.
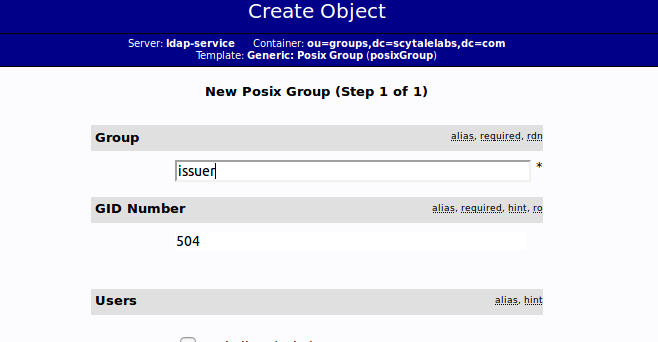
Repeat the process, but simply replace the “issuer” name with “revoker”, “employer” and “student”. Be sure to re-click the “ou=groups” entry before creating child entries, or else you may create entries under the wrong category.
You should now have four groups in the left-hand panel:
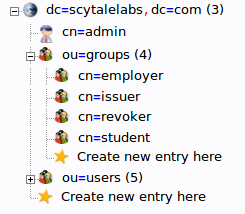
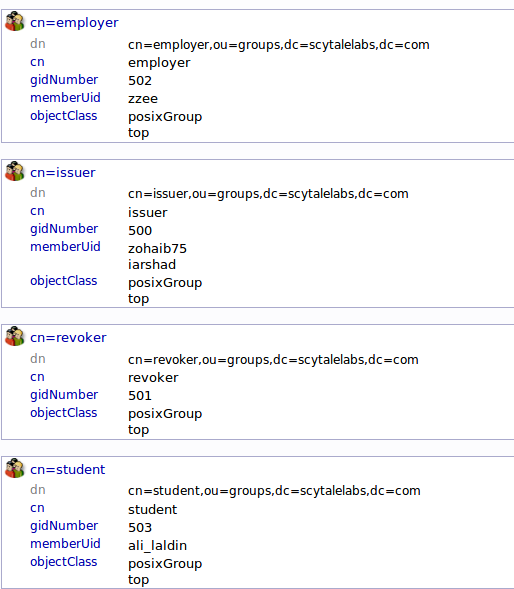
You can see an overview of the entries in the “ou=groups” category by clicking on that entry, and then clicking on “View 4 children”:
Create Users
Next, we will create users to put in these groups. Start by clicking the “ou=users” category. Click on “Create a child entry”.
We will choose “Generic: User Account” for these entries.
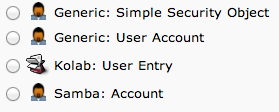
We will be given a lot of fields to fill out:
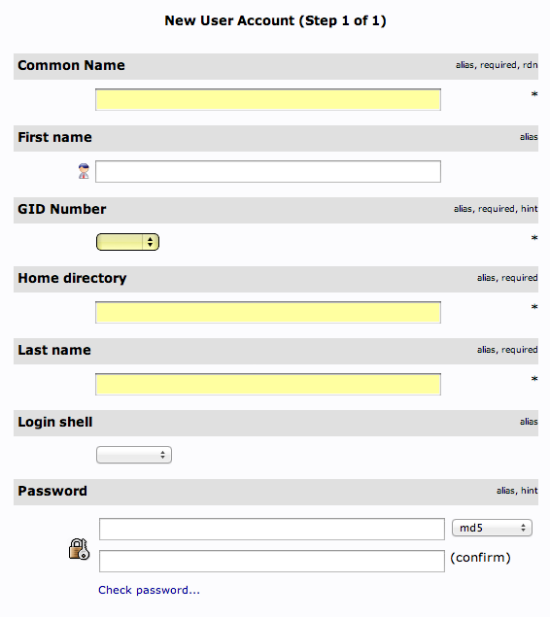
Fill in all of the entries with information that makes sense for your user.
Something to keep in mind is that the “Common Name” needs to be unique for each entry in a category. So you may want to use a username format instead of the default “FirstName LastName” that is auto-populated.
Click “Create Object” at the bottom and confirm on the following page.
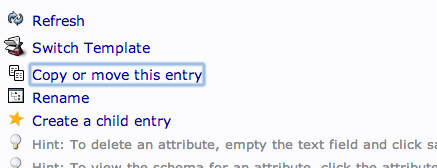
To create additional users, we will take advantage of the ability to copy entries.
Click on the user you just created in the left-hand panel. In the main pane, click “Copy or move this entry”:
Adjust the “cn=user” portion of the entry to point it to the common name you’d like to use for the new entry. Click “Copy” at the bottom:
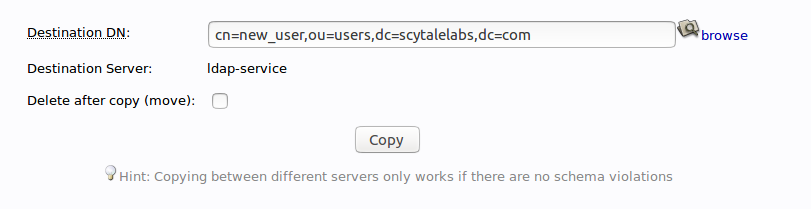
You will be given the next page populated with your first users data. You will need to adjust it to match the new users information.
Be sure to adjust the uidNumber. Click the “Create Object” button at the bottom.
Add Users to Groups
We can add users to various groups by clicking on the group in question. In the main pane, select “Add new attribute”:
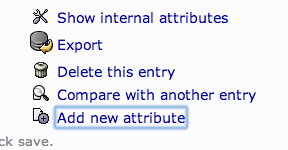
Select “memberUid” from the drop down menu:
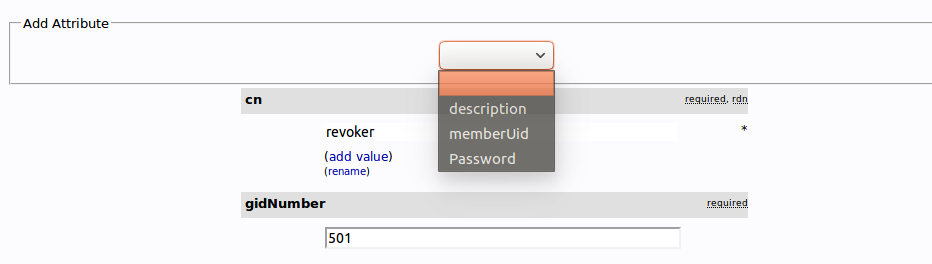
In the text field that populates, enter the first user you’d like to add. Click “Update Object” at the bottom:
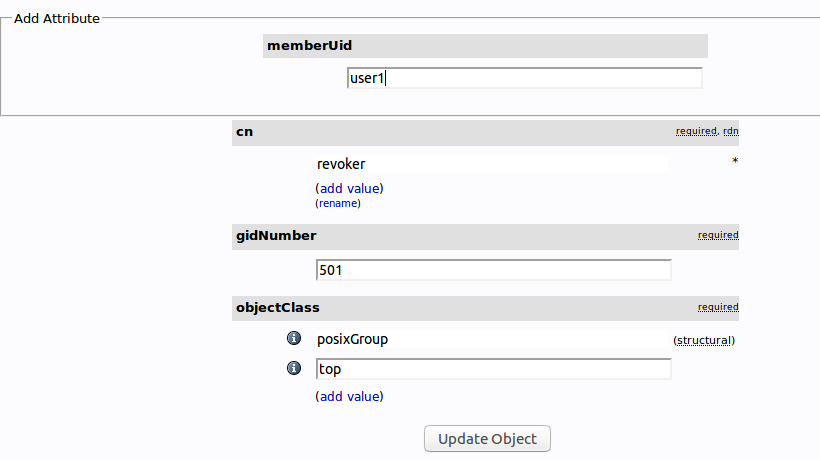
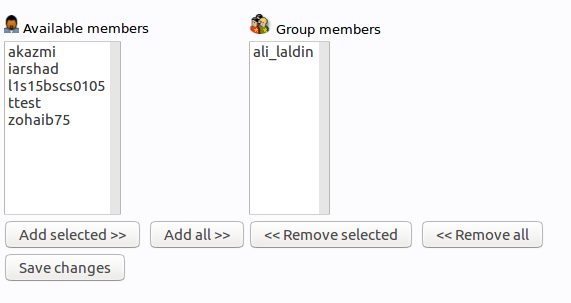
You can then add more members by clicking “modify group members” and selecting them from the available choices:
Conclusion
You should now have a basic LDAP server set up with a few users and groups. You can expand this information and add all of the different organizational structures to replicate the structure of your business.

